Google Cloud Platform Sources
Monitoring Source Technologies and Services that are Hosted on Google Cloud Platform (GCP)
Not Included in the BindPlane with Google Cloud Monitoring offering
All of the Google Cloud Platform sources listed within this documentation are not included with the BindPlane with Google Cloud Monitoring offering.
GCP Hosted Sources
Metrics are collected from the Google Cloud APIs for the various Google Cloud services.
Network Requirements
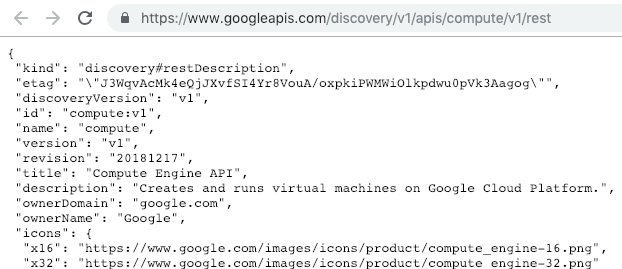
Metrics are via Google Cloud API Endpoints: https://googleapis.com/
Testing Network Access via this REST API call:
https://www.googleapis.com/discovery/v1/apis/compute/v1/rest
Least Privilege Users are defined in the following Source technology pages. You will find the permissions needed for each specific Source. We recommend a separate LPU is created for each Source type.
Example
Deploying LPU Roles with Google Cloud Deployment Manager - Recommended Method
The Google Cloud Deployment Manager can be used to deploy custom roles for a project, or an organization. This method include Master LPU's that can be used to create a single service user with permissions to monitor all the possible Google Services.
To deploy an individual role to a project, refer to this documentation:
Deploy individual roles to a GCP Project
To deploy an individual role to an organization, refer to this documentation:
Deploy individual roles to a GCP Organization
To deploy a master LPU role to a project, refer to this documentation:
Deploy a master LPU role to a GCP Project
To deploy a master LPU role to an organization, refer to this documentation:
Deploy a master LPU role to a GCP Organization
Google Cloud Identity and Access Management
Google Cloud users and service accounts must belong to a project. It is best practice to create a project just for the LPU users. Users can then be added to other projects using IAM.
The below steps have both Console (GUI) and GCloud CLI steps for either path.
Procedures:
- Create LPU Project
- Create Service Account
- Create role (either a project role or an organization role). This guide describes how how to create and organization role.
3a. Project roles are limited in scope (to the project they belong to)
3b. Organization roles are not limited in scope, and will grant permission to all projects belonging to the organization - Bind role to service account using IAM
- Add service account user to other projects using IAM
5a. This step can be ignored if the service account is using an organization role.
Create LPU Project
Console - Creating the LPU Project
To create a new project:
- Go to https://console.cloud.google.com/cloud-resource-manager
- On the drop-down at the top of the page, select the organization in which you want to create a project.
- Click Create Project
- In the New Project window that appears, enter a project name and select a billing account as applicable.
- If you want to add the project to a folder, enter the folder name in the Location box.
- When you're finished entering new project details, click Create.
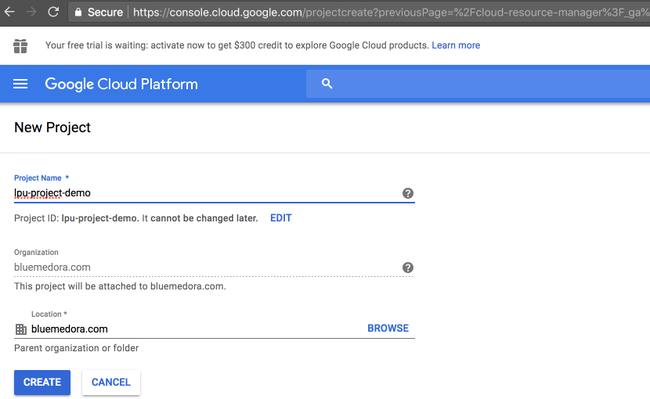
Creating the Google Project
GCloud CLI - Creating the LPU Project
To create a new project, use the gcloud projects create command:
gcloud projects create PROJECT_ID
Where PROJECT_ID is the ID for the project you want to create. A project ID must start with a lowercase letter, and can contain only ASCII letters, digits, and hyphens, and must be between 6 and 30 characters
To create a project with an organization or a folder as parent, use the --organization or --folder flags. As a resource can only have one parent, only one of these flags can be used:
gcloud projects create PROJECT_ID --organization=ORGANIZATION_ID
gcloud projects create PROJECT_ID --folder=FOLDER_ID
Create Roles
When an identity calls a Google Cloud Platform API, Cloud Identity and Access Management requires that the identity has the appropriate permissions to use the resource. You can grant permissions by granting roles to a user, a group, or a service account.
Create custom roles for each LPU at the organization level. Roles can be used for any project belonging to this organization.
Console - Creating Roles
To create a new custom role from scratch:
- Go to the Roles page in the GCP Console. https://console.cloud.google.com/iam-admin/roles
- Select your organization from the Organization drop-down.
- Click Create Role.
- Enter a Name, a Title, and Description for the role.
- Click Add Permissions.
- Select the permissions you want to include in the role and click Add Permissions. Use the All Services and All Types drop-downs to filter and select permissions by services and types.
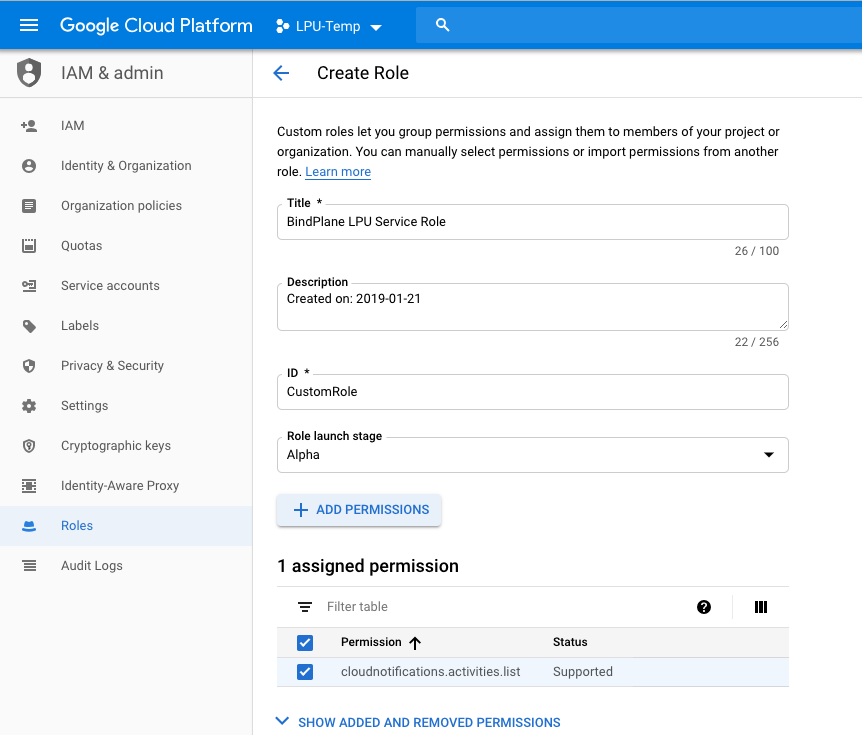
Using the Console to Create a Role the Project
GCloud CLI - Creating Roles
The following example YAML file demonstrates how to create a role definition. For each Source Technology in the subsequent pages, there is a listing of permissions that can be used to generate a similar YAML file for each Source that you want monitored.
title: "Role Viewer"
description: "My custom role description."
stage: "ALPHA"
includedPermissions:
- iam.roles.get
- iam.roles.list
Apply the Role YAML to the Project with the following:
gcloud iam roles create viewer --project my-project-id \ --file my-role-definition.yaml
Create a Service Account
When you create a new Cloud project, Google Cloud Platform (GCP) automatically creates one Compute Engine service account and one App Engine service account under that project. You can create up to 98 additional service accounts to your project to control access to your resources.
After creating the roles, we need to create a service account. Creating a service account is similar to adding a member to your project, but the service account belongs to your applications rather than an individual end user.
Console - Creating the Service Account
- Open the Service Accounts page in the GCP Console. Go to https://console.cloud.google.com/projectselector/iam-admin/serviceaccounts
- Click Select a project the lpu-project which you created in step 1
- Select your project and click Open.
- Click Create Service Account.
- Enter a service account name, select a role you wish to grant to the service account, and then click Save
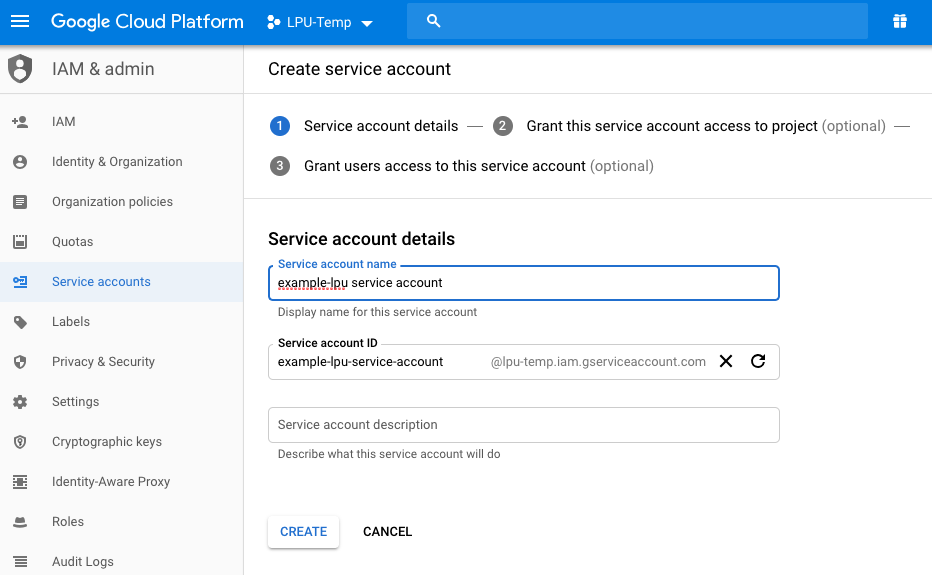
Creating a Service Account in Google Cloud Platform Console
GCloud CLI - Creating the Service Account
Creating service account using cli, Where SA = Service Account
gcloud iam service-accounts create [SA-NAME] --display-name "[SA-DISPLAY-NAME]" gcloud iam service-accounts list
Granting Roles to Service Accounts
When granting IAM roles, you can treat a service account either as a resource, or an identity. Your application uses a service account as an identity to authenticate to Google Cloud Platform services.You grant roles to a service account so that the service account has permission to complete specific actions on the resources in your Cloud Platform project.
Console - Granting Roles to Service Accounts
You can manage roles on service accounts the same way you manage roles on users in your project.
- Open the IAM & Admin page in the GCP Console. https://console.cloud.google.com/projectselector/iam-admin
- Select your project and click Continue.
- Identify the service account to which you want to add a role.
3a. If the service account isn't already on the members list, it doesn't have any roles assigned to it. Click Add and enter the email address of the service account.
3b. If the service account is already on the members list, it has existing roles. Click the drop-down list under Role(s) for the service account that you want to edit. - Select one or more roles to apply to the service account.
- Click Add or Save to apply the roles to the service account.
GCloud CLI - Granting Roles to Service Accounts
Example using the CLI to Grant Roles to the Service Accounts
gcloud projects add-iam-policy-binding my-project-123 \ --member serviceAccount:[email protected] --role roles/editor
Generate Service account credentials
To allow a user to manage service account keys, grant the Service Account Key Admin role roles/iam.serviceAccountKeyAdmin
Cloud IAM primitive roles also contain permissions to manage service account keys, but we recommend granting this role instead to prevent unnecessary access to other GCP resources.
Console - Generate Service account credentials
- Open the IAM & Admin page in the GCP Console. https://console.cloud.google.com/projectselector/iam-admin
- Select your project and click Continue.
- In the left nav, click Service accounts.
- Look for the service account for which you wish to create a key, click the More button in that row, and then click Create key.
- Select a Key type and click Create.
GCloud CLI - Generate Server account credentials
gcloud iam service-accounts keys create ~/key.json --iam-account [SA-NAME]@[PROJECT-ID].iam.gserviceaccount.com
Google Cloud CLI
You can use the Console or CLI method for administering the services accounts. For more information on getting started with the CLI see:
https://cloud.google.com/pubsub/docs/quickstart-cli
Updated almost 4 years ago
